by Gina Vlosky | Dec 14, 2020 | Case Studies, Private Equity
Download PDF Version
ABOUT FIRM
 Heritage Group is a Nashville-based, healthcare-focused investment firm with more than 30 years of experience financing and operating healthcare companies at all stages. The firm’s limited partners include leading hospital systems, payers and other healthcare organizations that operate over 10% of the hospitals in the U.S., insure over 45 million people and deliver pharmaceuticals and medical products to more than 100,000 locations daily.
Heritage Group is a Nashville-based, healthcare-focused investment firm with more than 30 years of experience financing and operating healthcare companies at all stages. The firm’s limited partners include leading hospital systems, payers and other healthcare organizations that operate over 10% of the hospitals in the U.S., insure over 45 million people and deliver pharmaceuticals and medical products to more than 100,000 locations daily.
CALL-TO-ACTION
In preparation for their third fund, Heritage sought a more robust CRM solution that would help to better track and manage relationships with the firm’s growing number of strategic investors.
Heritage also needed to make a decision about their investor portal. They were using their existing CRM provider’s portal solution, but felt it lacked the ease-of-use and mobile experience they wished to provide their LPs. Ideally, they wanted an integrated solution that would help reduce manual processes and create greater transparency with investors.
DECISION
Heritage ultimately chose DealCloud as their new CRM provider, along with SmartRoom, DealCloud’s investor portal partner, which could be integrated into the CRM platform. By connecting the two technologies they could reduce administrative work by managing all user provisioning and security settings within a single source.
PROCESS
After migrating from their existing CRM to DealCloud, Heritage was ready to set up their new investor portal with SmartRoom. They were assigned a dedicated SmartRoom Project Manager who worked alongside the Heritage team to help:
- Connect DealCloud: Liaison between the DealCloud team to ensure the integration between the two platforms was setup correctly, including security settings that control what fund/investor details are made available to any specific investor or contact.
- Customize Portal Experience: Setup the portal design to match Heritage’s branding and ensure the most optimal experience for all investors.
- Optimize Reporting Process: Understand the firms existing workflows to identify ways to drive greater efficiency with reporting tools and features.
“The level of customer service and support we’ve received from our project manager is a 10 out of 10. She has been instrumental in driving this entire process and making it all come together. She was there at every step, working through all the details to ensure we were up and running smoothly.”
– Florence Chassaignac, Director of Operations, Heritage Group
SOLUTION
Utilizing SmartRoom’s SmartLP reporting tools, Heritage was able to implement a new portal to automate and optimize:
- Financial Statement Distribution: Using the “SmartMove” tool, Heritage can now upload all investor financial statement documents into a secure, centralized folder and then automate their distribution into each individual investor’s designated portal.
- Capital Calls/Distribution Notices: Investor information can be mapped from fields in an excel file into a report template document to create customized PDF reports for each investor with the “SmartMerge” tool. It then automates their distribution into each individual investor’s designated portal.
- Investor Experience: Heritage can now deliver real-time fund information and dynamic reporting LPs can access through an intuitive portal anytime, anywhere.
RESULTS
SmartRoom helped Heritage Group:
- Streamline Workflows: Integrate SmartRoom and DealCloud technologies to eliminate redundancies and create a single source of truth for all investor management and provisioning.
- Save Time: Reduce administrative tasks and create a more efficient process across multiple types of investor correspondence.
- Improve LP Experience: Provide investors better accessibility to information they need.
“SmartRoom has helped streamline and simplify our entire process. We’ve saved a lot of time on capital calls and distributions, and expect to see even more time savings as we continue to optimize our workflows. I love how intuitive and organized the platform is. We’re happy we can deliver such a user-friendly experience to our LPs.”
– Florence Chassaignac, Director of Operations, Heritage Group
Click here for more information on SmartRoom’s Private Equity & Alternative Investment Solutions or Contact Us.
by Gina Vlosky | Sep 29, 2020 | Audits, Case Studies, Legal

ABOUT COMPANY
A leading insurance company (Insurance X)
The Property Casualty Audit Group at leading insurance company was responsible for completing over 30 audits during 2020. As part of the audit process, Insurance X needed to share large amounts of data with external 3rd party auditors. The data contained sensitive and confidential information, so security was paramount. To ensure complete control, Insurance X invited the external auditors to their offices to view the information in-person on the company’s internal servers.
COVID-19 CHALLENGE
When COVID-19 forced the company to close its offices and all employees were required to work from home, Insurance X could no longer host in-person viewings of the data with the external auditors. Since they were not employees of Insurance X, they could not be given access to the company’s servers. The group needed to find a new way for the auditors to view information they were privy to, while maintaining complete control of the data within a secure environment.
REQUIREMENTS
Insurance X needed a solution that could provide:
- Speed & Efficiency: Each audit involved large amounts of data, so they needed to quickly and easily upload files from their internal servers.
- Reliability: Total confidence that the solution met their stringent security requirements and would keep them in total control of the data at all times.
- View-Only Access: The ability to restrict print, download, save, and modification rights on all file types – including email (.msg) files and any corresponding attachments.
- Native File Access: Ensure that all data, including the emails and attachments, were made available to view in their native file formats.
SMARTROOM SOLUTION
Due to the format of Outlook .msg files types and associated attachments, finding a solution that could restrict saving and downloading these files proved challenging. The Property Casualty Audit Group sought out leading data room and content management providers to help manage the process. They were referred to SmartRoom by another team within Insurance X who had multiple successful and ongoing projects with the provider.
PROCESS
The group was assigned a designated project manager who worked with the team to understand their specific needs and ensure all requirements could be met. After some discussion, the SmartRoom team was able to come up with a solution to meet the requirements.
It was decided each audit would have an individual room. The group’s dedicated project manager assisted with setup and training. Together, they developed a customized process utilizing SmartRoom’s unique core features:
- Upload Tools: Multiple user-friendly upload tools allowed the group to upload data quickly and efficiently from the company’s internal servers.
- Securely Invite & Manage Users: The administrators were able to easily create and send user invitations to the auditors so they could securely access the room.
- Document-Level Security: Custom security profiles and granular security rights were setup so they could control access to any specific file for any user.
- SmartLock: SmartRoom’s proprietary application allowed files to be accessed in their native applications with total control of user’s rights. To meet the email & attachment restriction requirements, SmartRoom made some modifications to the application and customized a process for Insurance X – at no extra cost.
- Testing/Demo Rooms: SmartRoom created free demo rooms for each audit so the group could preview and test before inviting the external auditors.
RESULTS
COVID-19 no longer presented a barrier. SmartRoom helped The Property Casualty Audit Group at Insurance X:
- Save Time: SmartRoom’s rapid upload speeds allowed them to upload data faster than they did previously using their internal servers.
- Safeguard Information: They could rest assured that sensitive and confidential information was secure and in their control at all times.
- Enhance Auditor Relationships: The external auditors found SmartRoom user friendly & efficient – saving time & making their jobs easier.
- Streamline Audit Process: Both parties streamlined their entire audit process by eliminating costly and time consuming in-person viewings.
Contact us to learn how we can help streamline your audit process.

by Gina Vlosky | Sep 21, 2020 | Restructuring
Driven by the COVID-19 pandemic and the resulting economic slowdown, millions of jobs have been lost across the U.S. and around the world. Businesses of all sizes and in all industries are facing tough decisions about how to stay afloat, deliver for investors and be best positioned for the long term.
If you turn on CNBC or read the Wall Street Journal these days, the word that’s on the top of everyone’s mind is “restructuring.” In early August, Disney announced a $5 billion restructuring and impairment charge during their quarterly earnings call. Cisco, the technology giant, announced a $900 million charge and expects significant layoffs from its 75,000 person staff. The situation repeats itself at Deutsche Bank, Pfizer, Harley-Davidson and so many more. Even more visceral, perhaps, are the store closings, liquidations, bankruptcies (whether Chapter 7 liquidations or Chapter 11 restructurings, some of which file a second time, known in industry parlance as “Chapter 22” cases) and “Going out of Business” and “Everything must go” signage festooning malls, strip malls, and shopping promenades around the country.
In each of these situations, members of these companies administration, legal and finance teams (as well as lenders, retained professionals, the retained professionals of counter-parties, etc.) will need to review thousands of documents to ensure they are best prepared to successfully announce and implement a restructuring program. They’ll also need to negotiate directly with creditors, bondholders and lenders to streamline balance-sheets, operations and help them meet new goals, which are often a moving target. But, they need to do so in a safe and secure environment, helping to ensure employee and business information is protected and that word doesn’t leak out before the company formally announces plans, or prepares to transfer such data and Intellectual Property to a new owner. Under normal circumstances this can prove challenging; layer on the fact that most people are telecommuting due to COVID-19, this presents a whole series of other issues. This is where a virtual data room (VDR) can make all the difference.
So let’s take a look at some of the major benefits a VDR can provide for the development and implementation of a restructuring plan.
- Reduces Preparation Time: Timing is critical when it comes to an effective restructuring announcement and deployment. Should a restructuring become the necessary outcome of financial challenges, every day in which a new path forward is delayed, the impact on the bottom line is compounded. With a VDR, teams can work together in a structured and secure manner to determine what makes the most business sense, what the impact of each option is and how to proceed going forward. SmartRoom, one of the leading VDR providers, is designed to save time. It offers integrations with cloud storage systems like Box and Outlook, enabling users to directly upload files into the VDR. No time-consuming downloading and then uploading required. It also offers the proprietary SmartDrive application that allows users to work with SmartRoom content from the convenience of their desktop.
- Streamlines Due Diligence and Auditability: When it comes to due diligence and auditability, there’s no substitute for having documents in order. This is where a VDR like SmartRoom makes all the difference. It offers notifications and alerts on who is handling what documents and when. The proprietary SmartLock feature let’s you set time limits on data accessibility and remotely detonate documents even after they have been downloaded. Plus there’s the advance reporting features and dashboards that track every user and document activity.
- Security and Compliance: Data breaches are all too common these days. Whether they are phishing expeditions, cyber attacks or viruses, these types of attacks can compromise critical company information and employee data. And worse yet, they can grind company operations to a halt or even be used as part of a blackmail scam. VDRs all but stop these criminals in their tracks thanks to multi-level authentication and bank-grade encryption.
- “Need to know” basis: Sharing HR information with a prospective buyer, due-diligence party such as a lender, private equity or angel investors may be necessary, while the same information is best withheld from a strategic competitor who may be interested in simply learning as much as they can about a competitor. Additionally, an advanced VDR such as SmartRoom with granular user rights could protect salary information from people WITHIN the company who are not cleared to see their co-workers data, whether within a restructuring endeavor, or not, while outside professionals can manage the same information without those considerations. Consumer-grade platforms, or internal SharePoint or intranet can’t offer this capability.
- Streamlines Communication: With most people working remotely because of the pandemic, a system that organizes thousands of electronic files is crucial. VDRs offer precisely that. They help avoid the chaos and confusion resulting from a string of emails. Users will never have to worry about multiple drafts circulating around and wonder which is the right version of a particular document. VDRs like SmartRoom centralize files creating a single source of truth. Plus it records who accesses these files and notifies all involved of relevant updates. This eliminates confusion, double work and wasted time. Additionally, VDRS like SmartRoom offer a DocuSign integration, which handles contracts and non-disclosure agreements all securely within the data room.
- Reduces Costs: Time is money. Time will always be money. And during a restructuring, time and money are things that companies generally have limited amounts of. VDRs are designed to keep costs down because of the time savings and efficiencies they deliver. Savings are passed on to both the internal team, as well as for hourly billed professionals whose time is better spent than in a document chase, anyway.
Learn more about how SmartRoom’s virtual data room can help your business.
Sources:
Walt Disney Misses On Revenue As Theme Parks See $3.5 Billion Hit; Earnings Excluding Charges Beat Street; Media Networks, Studio Mixed
https://www.fiercetelecom.com/telecom/cisco-implements-restructuring-plan-including-layoffs-as-stock-tumbles-after-hours
https://www.cnbc.com/2020/07/29/deutsche-bank-q2-2020-earnings.html

by Gina Vlosky | Sep 9, 2020 | Latest News
By: Steve Lumer, SmartRoom Director of Sales and Business Development
It’s been a little over a month since I’ve joined SmartRoom, and one of the things I’ve learned is how we are helping many organizations with various use cases beyond sharing data for M&A and ABS sales.
As COVID-19 continues to affect the way business is conducted, SmartRoom can help. Not only can we empower your dealmakers to remain productive, we can also help your broader enterprise securely access, share, and manage content from any device. Our products and services are helping organizations across all industries with various use cases like the ones below.
- Education – SmartRoom is enabling one of the world’s largest universities to share education material with students so continued education can occur and professors can track which students are reviewing course materials.
- Audits – A large financial institution is conducting ongoing stress testing to ensure their balance sheets are in order. SmartRoom enables them to seamlessly share information with regulators.
- Corporate File Sharing – SmartRoom is assisting a large manufacturing facility with ad-hoc content sharing as their FTP portal has failed them.
- Restructuring & Claims Management – A leading energy firm is turning to us to assist with information sharing during a restructuring process & possible claims management.
- Structured Finance Transactions – A leading asset manager is sharing due diligence materials for a cross-border transaction because deal teams can’t currently be in one location.
- Investor Reporting – Private Equity firms rely on SmartRoom to share investor specific content and overall market summaries.
SmartRoom is so much more than just a virtual data room. I’d love to schedule time in the next coming weeks to learn a little more about your current information sharing workflows and see if SmartRoom can help.
Steve Lumer
[email protected]
917-533-0942
by Gina Vlosky | Jun 22, 2020 | Latest News, Private Equity
Embed This Infographic
Copy and paste the code below to get this infographic onto your website or blog.
CURRENT CONDITIONS
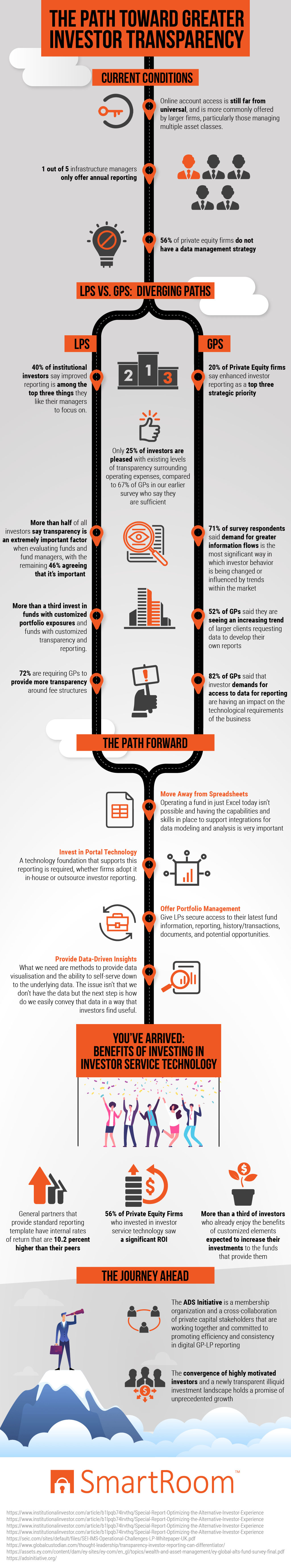
In spite of the incremental steps that have been taken in recent years to improve conditions, there continues to remain a large disparity between standard types of investing and private equity. Investors who place their dollars in a mutual fund, for example, are readily able to access information on every charge that they incur. There is no mystery when it comes to management and performance fees, which is in marked contrast to what private equity investors still experience.
This lack of transparency is evident in several ways. For one thing, access to information from online sources remains unavailable to a wide swath of investors. For many, data is only distributed once per year in the form of the annual report. This situation is made worse by the fact that over half of the country’s private equity companies have not yet come up with a strategy to effectively manage their data.
LPS VS. GPS: DIVERGING PATHS
Limited partners (LPs) are the external investors who contribute their capital into one or more of the funds that the firm handles. This type of structure is not designed for everyone; in fact, investors usually need to shell out at least $250,000 to participate. For that reason, many LPs are not individuals but instead may be foundations, university endowments, pension funds and the like. LPs are only liable for the amount they contribute to the fund, which is managed by the general partner.
Since LPs do not have a direct relationship with their invested monies, it stands to reason that these individuals and companies desire as much transparency in reporting as possible from the general partner who is responsible for managing them. When investors can get their hands on these valuable details on an on-demand basis, they are in a much better position to evaluate the general partner’s performance.
More than a third of LPs choose to have additional control over their funds with customized portfolio exposures. There are several types:
- Security constraints concern conditions that dictate which specific funds cannot be bought or sold and which are held or replaced. These conditions help to match client personal preferences, facilitate balanced portfolios and counterbalance various types of risk;
- Sector constraints help to determine whether funds should always or never be put into certain industries or types of companies;
- Social criteria or restrictions prevent investment in companies of which the client does not approve for religious, ethical or other reasons;
- Minimum or maximum amounts of cash to be invested.
In addition to these customizable features, almost three-quarters of all LPs want the GP with whom they work to be much more open about the types of fees they charge as well as the reasons for each.
General partners want to please the LPs they already have on board and attract more. They also understand that investors are not only demanding more information but are using it to shape the decisions they make. Therefore, it comes as no surprise that 20 percent of the survey respondents list enhanced investor reporting as an important emerging priority.
When today’s savvy LPs do not get the portfolio-related information they want in their desired amount or frequency, they tend to take matters into their own hands. In fact, more than half of the surveyed GPs report that their clients are starting to ask for the data necessary to create their own reports. As a result, general partners are being stretched in new ways, forced by the demands of LPs to find new technological vehicles to provide the information that is being requested.
This trend for requesting added transparency from GPs appears to be increasing in strength and urgency. Only a quarter of the LPs surveyed are happy with the status quo in this arena, a marked drop from the 67 percent of satisfied investors recorded in the past questionnaire.
THE PATH FORWARD
While Excel addresses basic data analysis and management needs, it falls short of the mark for the complex environment of private equity. Limitations include the following:
- Collaboration is difficult;
- Security is minimal;
- Multiple versions of documents can exist;
- Files can be easily corrupted, and it can be difficult to track who made the mistake;
- Instability;
- Difficulty in integrating data;
- Access constraints;
- Issues in creating comprehensive reports;
- Program is dated and clumsy.
It is far better for firms to integrate all of their information through the use of private equity or venture capital software that is suited to the particular needs and constraints of this specialized industry.
For either in-house or out-sourced reporting, portal technology aids in facilitating maximum transparency, security, reliability and visibility for LPs who want real-time access to their data. It provides information about fund performance, residuals, contributions and distributions directly from their funds’ official records. Thanks to this technology and office portfolio management software, they can expect flawless data visualization, access to underlying data in real time, performance reporting and secure delivery of documents.
Private equity firms are repositories for a vast store of data for their investors. Now that LPs are asking for enhanced access to this information, the challenge for firms lies in coming up with technological and communication strategies that will facilitate easy, real-time sharing of specifics about their granular underlying data.
When general partners take actions to meet investors’ requests for enhanced information about their data, positive results ensue. Internal rates of return are more than 10 percent higher, and return on investment (ROI) is increased for the majority of private equity firms who took the leap to use advanced investor service technology. Clients who are already benefiting from customized portfolios anticipate that they will invest additional funds with the private equity firm that has gone the extra mile to give them the specific reports and funding strategies that they request.
THE JOURNEY AHEAD
The Adopting Data Standards (ADS) Initiative consists of a network of private capital stakeholders. Their goals include the following:
- Coming up with a live, GP-LP proof-of-concept for reporting;
- Building consensus and promoting reporting efficiency and consistency;
- Arriving at a set of standards that are accepted worldwide;
- Fostering industry-wide engagement and participation in a “commercially neutral” initiative.
Thanks to this collaboration, a foundation of efficiency and transparency can be fostered among all of the stakeholders in the process.

 Heritage Group is a Nashville-based, healthcare-focused investment firm with more than 30 years of experience financing and operating healthcare companies at all stages. The firm’s limited partners include leading hospital systems, payers and other healthcare organizations that operate over 10% of the hospitals in the U.S., insure over 45 million people and deliver pharmaceuticals and medical products to more than 100,000 locations daily.
Heritage Group is a Nashville-based, healthcare-focused investment firm with more than 30 years of experience financing and operating healthcare companies at all stages. The firm’s limited partners include leading hospital systems, payers and other healthcare organizations that operate over 10% of the hospitals in the U.S., insure over 45 million people and deliver pharmaceuticals and medical products to more than 100,000 locations daily.




